Introduction
When the coronavirus pandemic became a widespread threat in the United States and employees had to pack up their things to begin working from home, the data security measures permitted by remote work were low on organizations’ lists of priorities. Leaders were, as they should have been, focused on their employees’ health. Yet, remote work generally poses greater security threats to organizations than in-person work since, for example, employees use home networks and access organizational information on personal devices.
Seven months later, the majority of arts organizations are still not able to open for normal operations or allow all employees to return for in-person work. This pattern is not expected to change for several more months, and many thought leaders project that remote work will remain as a choice for many.
Therefore, now is a good time for arts organizations to evaluate the cybersecurity measures they have in place for remote work. Even before the Covid-19 pandemic, cybersecurity was becoming a bigger threat for smaller organizations and nonprofits, so being aware of these issues can aid arts organizations’ long-term operations and potentially open the door for more remote work opportunities in normal times.
What is Cybersecurity?
According to Cisco, a networking hardware company, cybersecurity is “the practice of protecting systems, networks, and programs from digital attacks.” Digital attacks can take many forms and are not limited to hackers in dark basements trying to steal an organization’s classified information. Several types of attacks are based on social engineering, which tricks an employee into sharing information or taking an action, such as clicking on a link. These forms of attacks then often install malware, “a type of malicious software installed onto a computer or system without the consent or intent of the user.” [1] The following are four major types of social engineering attacks:
Baiting: A hacker takes advantage of an individual’s curiosity and uses a false promise to steal the user’s information or install malware. Baiters can accomplish this using hardware, such as a malevolent USB drive left around the office that, when plugged into a computer, compromises the system.
Phishing: In this type of attach, hackers send mass emails that include a message meant to trick users into divulging passwords or personal identifiable information (PII). The message might look suspicious and say something like, “click here to reset your password.”
Scareware: By convincing users that their systems have been compromised, hackers prompt them to secure their system by installing (malicious) software.
Spear Phishing: A form of phishing that targets a specific individual, organization, or business. This could be something like an email designed to look like it’s from your boss, as seen in the video below.
Figure 1: A dramatized example of a cyberattack unfolding using spear fishing. Source: Cisco.
Other types of attacks avoid the social engineering tactic and are designed to disrupt operations or compromise data. Examples of these types are:
Advanced Persistent Threat: “A sustained, embedded attack the strives to remain undetected, enabling surveillance, service disruptions, and data theft over a long period of time.” [2]
Denial of Service: An attack that blocks users from information system resources or services.
Man-in-the-Middle: Hacker inserts themselves between client and server to collect information the individual sends. This can happen, for example, between an unsecured Wi-Fi hotspot and an individual’s computer.
Data Extraction Attack: A hacker executes a SQL query to a database using the input data from the client to the server. If they are successful, the hacker can access all the information in the database, modify it, or delete it.
Ransomware: A type of malware that threatens to publish its target’s data or permanently block access to it unless the victim pays a ransom. This particular type of cyberattack has been on the rise during the Covid-19 pandemic.
To protect against these attacks, an arts organization would need to prevent outside access to its data, IT systems, and programs. While employee awareness and training can go far to protect against social engineering attacks, organizations may have to implement more technology-based solutions to prevent against attacks intended to disrupt operations or compromise the data in a system.
Why Should Arts Nonprofits Care?
While nonprofit arts organizations may not see themselves as potential targets of cyberattacks since their servers do not hold government secrets, for example, there are many reasons why hackers would want to gain access to their systems. One reason is that nonprofit arts organizations store data about high-profile, wealthy donors that is attractive to bad actors. Other times, hackers are just trying to make money, as in the case of a ransomware attack, and know that smaller nonprofits would be easy targets since they have fewer resources to protect against cyber threats.
There are also risks to arts organizations outside of their small nonprofit status. In May 2020, anonymous hackers completed a ransomware attack on the third-party cloud software company Blackbaud and gained access to the personally identifiable information (PII) of donors to several hundred cultural institutions, including the Smithsonian Institution and the National Trust. Many arts nonprofits store sensitive information about patrons and donors using third-party software, leaving the data’s protection outside of their direct hands. Selecting a secure system is of incredible importance. Even when organizations are able to retrieve their files and no PII is shared publicly after an attack, the knowledge that an organization is vulnerable to these types of attacks leads to a loss in trust in the institution from donors and the public.
Image 1: Visitors at a museum. Source: Pixabay.
Risks Caused by the Covid-19 Pandemic
The Covid-19 pandemic and widespread implementation of remote work has exacerbated the need for cybersecurity policies and procedures. Because the onset was abrupt, arts organizations did not have the chance to make sure there were procedures in place to create the most secure remote working systems.
Remote work creates risk because employees access organizational information on personal devices in the case that they did not bring a work computer home (which is often true with arts organizations’ limited resources) and use their home or public networks to work. Both personal devices and alternative networks are less secure than what employees would use in the office. According to Sean Mooney with Cybereason, “personal devices often lack the strong antivirus software, customized firewalls, and automatic online backup tools built in to business networks.” Additionally, many people do not change their home router password after it is first installed, leaving their entire home network vulnerable.
Since people are more digitally connected during the pandemic, there has been an alarming increase in cyberattacks. According to the FBI, its Cyber Division is receiving as many as 4,000 complaints of cyberattacks a day—a 400% increase from before the pandemic. This increase includes coronavirus-themed phishing and other social engineering attacks, which prey on people’s fears and vulnerabilities. Since many people are online all the time, it is generally easier for hackers to successfully execute cyberattacks. Arts organizations need to be aware of this environment as they continue to work from home and develop plans to do so more securely.
Overview of Solutions
Since many arts organizations are continuing to work from home, and remote work seems to be sticking around in some capacity for the foreseeable future, arts organizations should start implementing some basic solutions to increase cybersecurity. Solutions are not just about spending money on new technological solutions; human action also plays a major role in making remote work more secure. Below is a general overview of the steps arts nonprofits can take towards stronger cybersecurity.
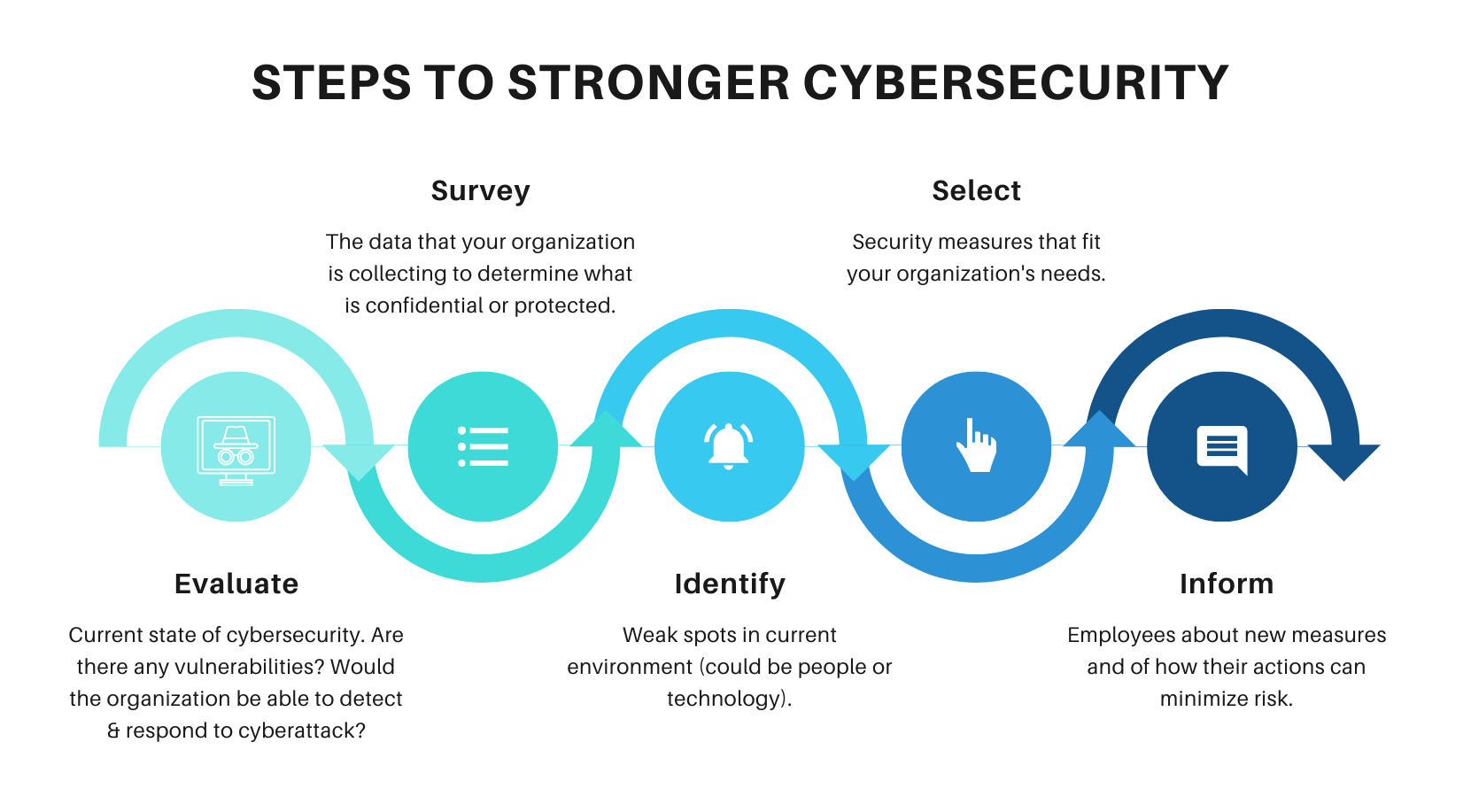
Figure 2: Infographic showing steps to stronger cybersecurity. Source: Author.
As indicated in the first step of the infographic, now would be a good time for arts managers to evaluate the cybersecurity protections offered by software they are already using. While, in the Blackbaud case, the company handled the breach swiftly and paid the ransom, Tyler Cohen-Wood, a cyber-security consultant and the former cyber deputy chief of the Defense Intelligence Agency, pointed out that Blackbaud merely took the hackers’ word that the copy of the stolen data was destroyed. To find a software company that is reliably secure, according to Artnet, “[Cohen-Wood] advises that museums employing third-party providers familiarize themselves with the company’s procedures for handling ransomware attacks and to have secure data backups, even if that means paying extra.”[3]
In an upcoming post about what cybersecurity measures arts organizations should have in place for remote work, I will include specific recommendations based on what a selection of arts organizations are doing. For now, an easy first action that arts organizations could take is asking employees to be more vigilant with the emails they are sending and receiving with the knowledge that the pandemic has led to an increase in phishing attacks. Organizations could also remind employees to have strong passwords on their home networks, personal devices, and accounts.
In general, some basic solutions for work-from-home security problems that arts organizations commonly face are cloud storage, virtual private networks (VPNs), password managers, multi-factor authentication, and mobile device management (MDM).
Cloud storage, when chosen well, provides a secure way for all employees to access files remotely.
VPNs “bypass geographic restrictions on streaming sites and other location-specific content” and provide a more secure way to access information by encrypting all internet traffic, making it unreadable to anyone who intercepts it.[4]
Password managers and multi-factor authentication both add extra layers of security to employees’ individual passwords
Mobile device management solutions allow for “the remote implementation of a number of security measures, including data encryption, malware scans, and wiping data on stolen devices.”[5]
CONCLUSION
It may seem fatalistic to ask arts organizations to prepare for the worst cyberattack situation—one that might seem unlikely—but managers should think of cybersecurity as another aspect of making their organization stronger, just like ensuring patrons’ physical safety and protecting the organization’s financial health. Now that the pandemic has forced many aspects of arts organizations’ operations online, managers can use this opportunity to survey their organization’s digital landscape.
[1] Afua Bruce, Cybersecurity for Nonprofits: A Guide, NTEN, February 2020.
[2] Bruce, Cybersecurity for Nonprofits: A Guide, NTEN.
[3] Sarah Cascone, “Hackers Have Stolen Private Information From Donor Lists to 200 Institutions, Including the Smithsonian and the UK’s National Trust,” ArtNet News, September 2, 2020, https://news.artnet.com/art-world/hackers-hit-smithsonian-parrish-corning-1905256.
[4] Sean Mooney, “Cyber Security Tips For Allowing Employees To Work From Home,” Cybereason, August 20, 2020, https://www.cybereason.com/blog/cyber-security-tips-for-allowing-employees-to-work-from-home.
[5] Mooney, “Cyber Security Tips For Allowing Employees To Work From Home.”
+ Additional Resources
Batti, Khadim. “Council Post: How Technology Could Impact The Workplace Over The Next Decade.” Forbes, February 6, 2020. https://www.forbes.com/sites/forbestechcouncil/2020/02/06/how-technology-could-impact-the-workplace-over-the-next-decade/.
Bednarski, P.J. “3 Wireless Giants Offer Their Own Password Manager App.” MediaPost, September 21, 2020. https://www.mediapost.com/publications/article/355943/3-wireless-giants-offer-their-own-password-manager.html.
Bruce, Afua. Cybersecurity for Nonprofits: A Guide. NTEN, February 2020.
Cascone, Sarah. “Hackers Have Stolen Private Information From Donor Lists to 200 Institutions, Including the Smithsonian and the UK’s National Trust.” ArtNet News, September 2, 2020. https://news.artnet.com/art-world/hackers-hit-smithsonian-parrish-corning-1905256.
Chenkin, Sam. “Is cybersecurity keeping you up at night?” NTEN, August 13, 2019. https://www.nten.org/article/cybersecurity-for-staff/.
Cisco. “What Is Cybersecurity?” https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html.
Clolery, Paul. “Breaking: Blackbaud Hacked, Ransom Paid.” The NonProfit Times, July 16, 2020. https://www.thenonprofittimes.com/npt_articles/breaking-blackbaud-hacked-ransom-paid/.
Co, Chris. “The basics of multi-factor authentication and single sign-on.” NTEN, January 10, 2019. https://www.nten.org/article/the-basics-of-multi-factor-authentication-and-single-sign-on/.
Cybereason. Guide: How To Maintain Secure Business Continuity With A Remote Workforce. https://www.cybereason.com/hubfs/2020_How_to_Maintain_Secure_Business_Continuity_with_a_Remote_Workforce.pdf.
Cybersecurity & Infrastructure Security Agency. “Stop. Think. Connect. Toolkit.” Accessed September 28, 2020. https://www.cisa.gov/publication/stop-think-connect-toolkit.
Dettbarn, Jason. “Remote Work Raises New Cybersecurity Challenges: Steps to Reshape Your Approach.” Info Security Magazine, July 29, 2020. https://www.infosecurity-magazine.com:443/opinions/remote-work-challenges/.
“Digital Tools for Artists to Run a Remote Career During Coronavirus.” Artwork Archive. https://www.artworkarchive.com/blog/digital-tools-for-artists-to-run-a-remote-career-during-coronavirus.
EY Belgium. “Why remote working will be the new normal, even after COVID-19.” EY, September 7, 2020. https://www.ey.com/en_be/covid-19/why-remote-working-will-be-the-new-normal-even-after-covid-19.
Hulshof-Schmidt, Robert. State of Nonprofit Cybersecurity. NTEN, November 2018. https://www.nten.org/wp-content/uploads/2018/11/Cybersecurityreport2018NTEN.pdf.
Idealware. What Nonprofits Need to Know About Security: A Practical Guide to Managing Risk. January 2016, https://offers.techimpact.org/reports/nonprofits-need-know-security-practical-guide-managing-risk/.
Lagana, Katherine. “Four things you need to know to protect against cyber threats.” NTEN, April 24, 2020. https://www.nten.org/article/four-things-you-need-to-know-to-protect-against-cyber-threats/.
Larson, Barbara, Susan Vroman, and Erin Makarius. “A Guide to Managing Your (Newly) Remote Workers.” Harvard Business Review, March 18, 2020. https://hbr.org/2020/03/a-guide-to-managing-your-newly-remote-workers.
Lynch, Jim. “Cloud Basics for Nonprofits and Libraries.” TechSoup, February 23, 2012. http://www.techsoup.org/support/articles-and-how-tos/cloud-basics-for-nonprofits-and-libraries.
Microsoft Philanthropies. Nonprofit Guidelines for Cybersecurity and Privacy. 2017. https://cdn2.hubspot.net/hubfs/575821/Nonprofit_Guidelines_for_Cybersecurity_and_Privacy.pdf?utm_campaign=IT%20Security&utm_medium=email&_hsmi=59307002&_hsenc=p2ANqtz-8dwheE_2oC1FojeSAGNJLY2HeZlAKlL09Ua3YaK1P-QJSKyXea2g6ushFPbr0H6n9uQHXV3-7z82_10YHdWo2_aSB2nw&utm_content=59307002&utm_source=hs_automation.
Minervini, Marco, Darren Murph and Phanish Puranam. “Remote Work Doesn’t Have to Mean All-Day Video Calls.” Harvard Business Review, September 9, 2020. https://hbr.org/2020/09/remote-work-doesnt-have-to-mean-all-day-video-calls.
MonsterCloud. “Top Cyber Security Experts Report: 4,000 Cyber Attacks a Day Since COVID-19 Pandemic.” Cision: PR Newswire, August 11, 2020. https://www.prnewswire.com/news-releases/top-cyber-security-experts-report-4-000-cyber-attacks-a-day-since-covid-19-pandemic-301110157.html.
Mooney, Sean. “Cyber Security Tips For Allowing Employees To Work From Home.” Cybereason, August 20, 2020. https://www.cybereason.com/blog/cyber-security-tips-for-allowing-employees-to-work-from-home.
National Council of Nonprofits. “Cybersecurity for Nonprofits.” Accessed September 28, 2020. https://www.councilofnonprofits.org/tools-resources/cybersecurity-nonprofits.
Nield, David and Brian Turner. “Best MDM solutions in 2020: Mobile Device Management for BYOD policies.” TechRadar Pro, August 6, 2020. https://www.techradar.com/best/best-mdm-solutions.
Nimishakavi, Sheela. “Nonprofit Cybersecurity: Why Pay Attention?” Nonprofit Quarterly, June 8, 2017. https://nonprofitquarterly.org/nonprofit-cybersecurity-pay-attention/.
NTEN. “IT security: a Q&A with expert Leon Wilson.” April 19, 2017. https://www.nten.org/article/it-security-a-qa-with-expert-leon-wilson/.
O’Sullivan, Fergus. “What Exactly is Zero-Knowledge in The Cloud and How Does it Work?” Cloudwards, July 6, 2020. https://www.cloudwards.net/what-exactly-is-zero-knowledge-in-the-cloud-and-how-does-it-work/.
Rivas, Dan. “Assessing risk: How to protect your most valuable data.” NTEN, March 21, 2016. https://www.nten.org/article/assessing-risk-protect-valuable-data/.
Schneider, Tim. “The Gray Market: How a Work-From-Home Revolution Will Change Galleries’ Relationships With Their Landlords Forever (and Other Insights.” ArtNet News, May 18, 2020. https://news.artnet.com/opinion/work-from-home-real-estate-1863447.
Schneider, Tim. “The Gray Market: Why History’s Biggest Work-From-Home Experiment Could Eventually Benefit the Art Market (and Other Insights.” ArtNet News, March 23, 2020. https://news.artnet.com/opinion/work-from-home-art-market-1811550.
Sharton, Brenda. “Will Coronavirus Lead to More Cyber Attacks?” Harvard Business Review, March 16, 2020. https://hbr.org/2020/03/will-coronavirus-lead-to-more-cyber-attacks.
Shepherd, Ash. “We’re all working from home. How do we do that effectively?” NTEN, March 19, 2020. https://www.nten.org/article/were-all-working-from-home-how-do-we-do-that-effectively/.
Stockton, Ben. “Best Cloud Storage for Nonprofits 2020: Quid Pro Quo.” Cloudwards, June 15, 2020. https://www.cloudwards.net/best-cloud-storage-for-nonprofits/.
U.S. Bureau of Labor Statistics. “Table 6. Employed persons working at home, workplace, and time spent working at each location by full- and part-time status and sex, jobholding status, and educational attainment, 2019 annual averages.” Last modified June 25, 2020. https://www.bls.gov/news.release/atus.t06.htm.
Wroblewski, Alyssa. “The Present & Future Of Arts Organizations, Technology, And The Pandemic.” AMT Lab, June 2, 2020. https://amt-lab.org/blog/2020/5/the-present-amp-future-of-arts-organizations-technology-and-the-pandemic.