Blockchain technology holds great potential for a wide variety of industries. To understand what opportunities the technology may hold for the arts field, and its potential for individual organizations, it is essential to understand the basic technology and the risks and opportunities it presents. In this three part series, we will detail how blockchain works (part 1), its applications for the arts (part 2), and the risks arts managers should consider before deploying a blockchain based system (part 3).
Blockchain Basics
Satoshi Nakamoto, the alias of an anonymous programmer, created blockchain for use in cryptocurrencies, such as Bitcoin.[1] Blockchain was designed to solve the Byzantine problem, essentially the challenge of ensuring that cryptocurrencies are not double spent.[2] To address this problem blockchain stores transaction data in a distributed ledger system where each user has a full copy of every transaction, each transaction is verified by each computer storing the ledger, and any alterations to the record are rejected by the network of linked ledgers.[3] This creates an immutable transaction history for each cryptocurrency. Any attempts to double spend coins or fraudulently alter balances will be rejected as other computers check the ledger history to verify the transaction.[4]
Creating a Blockchain
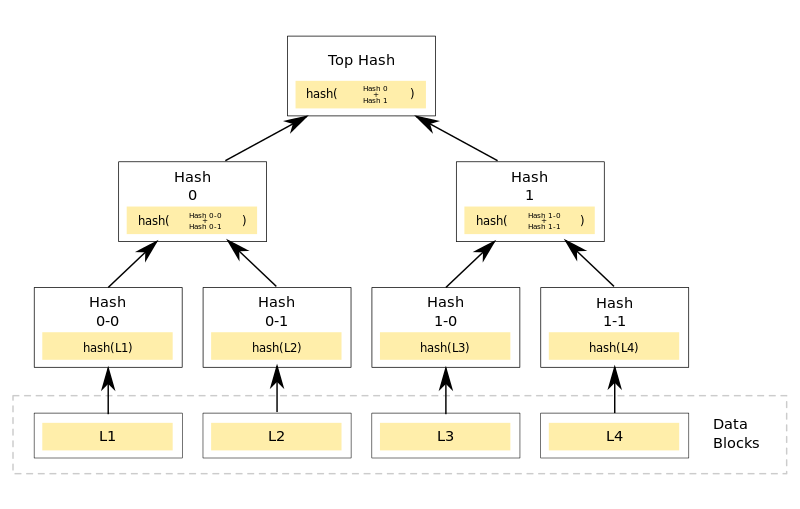
Figure 1: Merkle tree framework (Wikimedia commons)
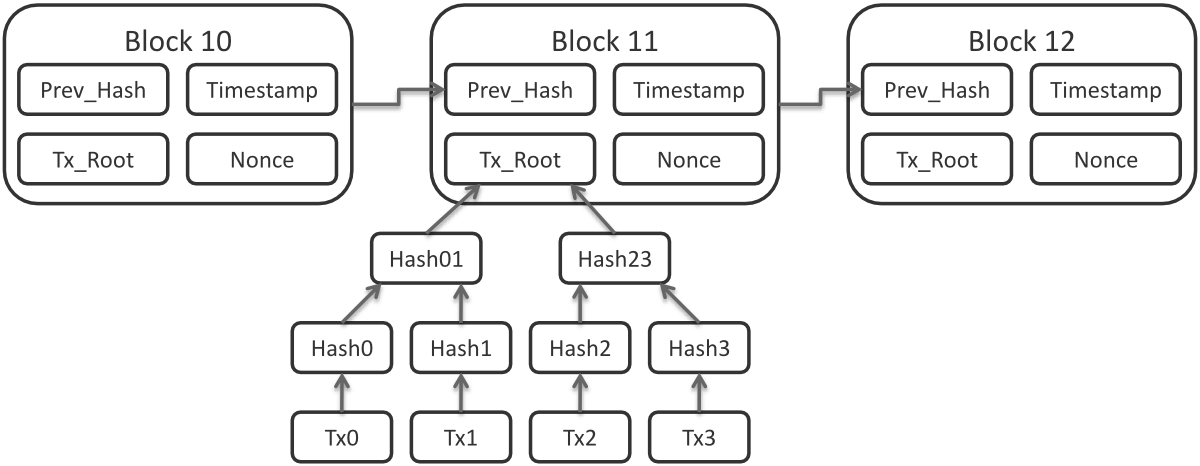
Every blockchain begins with a genesis block. This block contains the original set of transactions or data. To create, or ‘mine,” a block a group of submitted transactions or data are gathered, and each one is assigned a hash value.[5] A hash value is a form of encryption that assigns a unique string of characters for each data input.[6] Groups of hashed transactions are layered together in Merkle trees (Figure 1) which result in one final block hash value for the entire collection of transactions.[7] In order to be added to the blockchain the final block hash must conform to certain numeric and character requirements that are set by the blockchain creators, and are changed at set intervals. These requirements present a puzzle to be solved, which means that data is often hashed in thousands of ways by many computers independently trying to create the block before a final block’s hash characters match the parameters required to be added to the blockchain. Once one computer believes it has hashed the data in a manner which meets the requirements, it sends its solution to every other computer on the chain to verify the solution.[8] If it is correct, the block is added onto the blockchain by listing the block hash, the block hash of the previous block, the timestamp, and other relevant data on the distributed ledger (Figure 2). The user who successfully adds a block to the blockchain will typically receive a reward such as cryptocurrency. All the other computers who were trying to solve the previous block’s requirements release the transactions they were working on, pull fresh transactions from a queue of submitted transactions, and begin to hash them to try to create the next block.
Figure 2: Linking blocks together and the underlying Merkle tree (CC3.0 Matthäus Wander)
This type of verification, called “proof of work,” is the system deployed on the Bitcoin blockchain. It is designed specifically for systems that are “trustless” and do not utilize third party verification. For blockchains where there is some inherent trust between members other block adding styles, such as “round robin,” where computers add blocks in assigned turns, and “proof of stake,” where block creation is assigned with a frequency based on a user’s stake in the system, are utilized. These alternate methods of block adding do not require the competitive solving of a cryptographic puzzle in order to add a block to the chain, but otherwise employ the same basic blockchain tenants such as diversified ledger storage, cryptographic hashing, and Merkle trees.
Blockchain’s use and creation may be permissioned or permissionless. The most well-known blockchain, the Bitcoin blockchain, is a permissionless blockchain. This means that anyone can view the entire ledger and enter new transaction data. Most cryptocurrencies operate on permissionless blockchains. Alternately, permissioned blockchains limit the ability to read or input data to specific parties. Permissioned blockchains are typically found in private business and government settings.
Blockchain’s Near Immutability
The blockchain creation process means that data stored on the blockchain is nearly impossible to change. If a user alters data that is stored on the blockchain in any manner, when saved, that data will result in a new hash value. This new hash value will subsequently change the hash values all the way up the Merkle Tree, resulting in a new hash value for the entire block. When a computer attempts to put the block “back” on the blockchain all the other computers storing the blockchain will reject it because the hashed value for the block does not match the hashed value of the block that goes in its place.[9] The result is a system where hashed data cannot be deleted, altered, or changed in any manner. Further, because the ledger is distributed in full across many users, should the ledger be damaged or destroyed in any one location, hundreds or thousands of backup copies are readily available.
The permanence of data stored on the blockchain is the heart of its appeal, yet it is also the programs Achilles heel. Incorrectly input data cannot be changed, and fraudulent transactions cannot easily be fixed. For example, in 2016 a bug in the code of the Ethereum blockchain resulted in nearly $60 million of the ether cryptocurrency being siphoned by criminals.[10] In order to correct the situation the developers instituted a “hard fork” and reset the blockchain to the block before the siphoning began.[11] A group of users rejected the fork on moral grounds and continued to use the fraudulent chain.[12] This bifurcated chain resulted in two currencies being used on the platform instead of one.[13]
There are other actual and theoretical ways to compromise blockchain’s immutability. Some alterations are generally malevolent, such as a 51% attack, which would force the acceptance of an altered block. Other methods, like chameleon hashes, and administrative controls resulting in “scarred” blocks[14], are designed to allow blockchains to comply with data privacy laws and business needs. Method of altering a blockchain are controversial, and sometime criminal, as they undermine data integrity.
Environmental Impact
Running a proof of work blockchain requires an enormous amount of energy. Currently, the Bitcoin blockchain alone is estimated to consume almost as much energy as Ireland.[15] Latest estimates calculate that by the end of 2018 bitcoin mining will represent half the world’s energy consumption. As a result, one of the most widespread malware programs out today acts as a parasite on unsuspecting computers to use their energy to mine bitcoins.[16]
The Bitcoin blockchain is a permissionless blockchain which relies on the proof of work block validation method. Other validation methods, such as proof of stake and round robin require significantly less energy because they do not rely on multiple computers attempting to simultaneously solve a cryptographic puzzle.
Further, for companies deploying a private blockchain the hardware requirements are significantly greater than those of a centralized system. In order to achieve the high level of redundancy needed to provide benefits beyond a centralized system a blockchain needs to be stored on hundreds, if not thousands of networked computers. Ideally these computers would be stored in various locations to prevent total loss due to fire or other catastrophic possibilities. The increased technology costs may be significantly greater that the security benefits.
Part 2 of 3: Blockchain Applications for the Arts
Can’t wait? Check out:
Opportunities of Blockchain: What Arts Managers and Technologists Need to Know
Blockchain: The Tech Behind Bitcoin Opens Doors for Art Institutions
References:
[1] Pooley, Gale L and Lee, Larissa, “YOUNG LAWYERS DIVISION: BITS AND BLOCKS: NAVIGATING THE LEGAL LANDSCAPE OF THE BLOCKCHAIN ECONOMY,” Utah Bar Journal 31 (2018): 54.
[2] “Satoshi Nakamoto,” Wikipedia, https://en.wikipedia.org/wiki/Satoshi_Nakamoto. (last visited Jun 26, 2018).
[3] Arrunada, Benito, “Blockchain’s Struggle to Deliver Impersonal Exchange,” Minnesota Journal of Law, Science & Technology 19 (2018): 58-61.
[4] Ibid.
[5] Beyond Bitcoin: Emerging Applications for Blockchain Technology, Testimony before the Comm. on Science, Space, and Tech. Subcomm. on Oversight & Subcomm. on Research and Tech., H.R. Ser. No.115-47, 105th Cong. 2 (2018) (Testimony of Chris Jaikaran, Analyst in Cybersecurity Policy, Government, and Finance Division, Congressional Research Services).
[6] Ibid.
[7] Ibid.
[8] Thompson, Collin, “How Does the Blockchain Work? (Part 3),” https://medium.com/blockchain-review/what-blockchain-should-we-use-6ba9cca8df22, (last visited June 25, 2018).
[9] See H.R. Ser. No. 115-47.
[10] Arrunada, Blockchain's Struggle, 67-76.
[11] Ibid.
[12] Ibid.
[13] Ibid.
[14] "To Edit or Not to Edit: That's the Blockchain Question – Accenture, " The Future of Work | Accenture, Accessed June 28, 2018. https://www.accenture.com/us-en/insight-perspectives-capital-markets-edit-blockchain-question.
[15] Lee, Timothy B., Seniorius Lurkius, and UTC, "New Study Quantifies Bitcoin's Ludicrous Energy Consumption," Arts Technica, May 17, 2018, Accessed June 28, 2018. https://arstechnica.com/tech-policy/2018/05/new-study-quantifies-bitcoins-ludicrous-energy-consumption/.
[16] Grimes, Roger, “Hacking Bitcoin and Blockchain,” Dec. 12, 2017, Acessed June 28, 2018, https://www.csoonline.com/article/3241121/cyber-attacks-espionage/hacking-bitcoin-and-blockchain.ht