Cybersecurity has been on more people’s radars because of the recently exposed SolarWinds cyberattack, which impacted customers including the United States government. In this particular case, the breach was able to go undetected for months, indicating that even institutions with the highest levels of security can fall victim. As we begin the new year, arts organizations face a timely opportunity to consider their cybersecurity measures for remote work.
Introduction
Remote work creates more cybersecurity risks than when employees are in the office. When working away from the office, employees have to access sensitive information from outside of the network and, because employees are dispersed, it is more difficult to standardize what security measures the organization has for its employees.
The coronavirus pandemic has exacerbated this situation since widespread, long-term remote work came unexpectedly in March for businesses across the United States and they did not have the time to plan for the most secure situation possible. The arts nonprofit sector was particularly hard-hit by this scenario since strong cybersecurity measures are not the norm in this industry and because many organizations lack the resources—both monetarily and in expertise—to adapt their cybersecurity abruptly. According to NTEN’s State of Nonprofit Cybersecurity report from 2018, over 25% of surveyed nonprofit organizations had less than a full-time person in their IT staff. Furthermore, a little over 15% said that no one in their organization was responsible for IT.
As a follow-up to my previous research addressing why arts organizations should be thinking about cybersecurity for remote work, in this article, I will address specific solutions for arts organizations striving to make their remote work environment more secure. Based on research and interviews with IT and cybersecurity professionals working in arts nonprofits, there are four main recommendations for enhancing cybersecurity, each with a variety of specific solutions. They are:
Conducting a remote security risk assessment
Ensuring secure network access
Implementing policies and procedures for using personal devices, and
Training employees on best practices.
Figure 1: Visualization of cybersecurity solutions. Source: Author.
1. Conducting a remote security risk assessment
To determine what measures best fit an organization, managers need to know what, exactly, the organization is protecting and where they are vulnerable. Organizations should identify what sensitive information they store and where. This information could include the personally identifiable information (PII)—such as names, addresses, social security numbers, or credit card numbers—of donors or artists. NTEN’s State of Nonprofit Cybersecurity reports that a majority of nonprofits either do not have or do not know if they have a policy that clearly defines what data collected are considered PII. In our current technology-driven society, assets do not only include money and original artworks. According to an arts nonprofit professional getting his doctorate in cybersecurity, arts organizations need to realize that their data is gold. Nonprofit arts organizations may not see themselves as likely targets for a cyberattack, but because they often collect sensitive information about high-level donors, for example, they need to know where and how they are storing and protecting that data.
“Arts organizations need to realize that their data is gold.”
For organizations that are not sure where to start, they can take this free Compliance Audit Readiness Assessment from KnowBe4. Although users are required to provide their information, the results can provide a good benchmark. Tech Impact’s recently-updated Nonprofit Technology Policy Workbook provides a more extensive self-evaluation to help nonprofits identify the policies they need and find ways to start developing and implementing them.
One solution to ensure that no cyber attackers have access to an organization’s most sensitive data is simply by not storing it and having strict procedures for how to accept it. In this remote work environment, arts organizations may encounter more sensitive information sent digitally. A vice president of IT for a museum system said that they do not store any credit card numbers in their system to avoid keeping information that hackers would want. Although this can cause some inconveniences for donors and ticket buyers, the museum thinks it is worth it to keep their system the most secure. Another smaller organization pointed out that, while they do often encounter donors wanting to send sensitive information over email and contractors providing their social security numbers in a PDF form, they put a policy in place for employees who receive such information that includes either taking the information over the phone or using a password-protected way to send the file.
2. Ensuring secure network access
If an organization has evaluated what data it is collecting and storing, they can then make sure that employees have a secure way to access the information they need to do their jobs remotely. While cybersecurity is extremely important, employees do still need to have a functional way to access the information they need to do their jobs effectively. Three options that arts nonprofits can use to ensure secure remote access are multi-factor authentication (MFA), cloud storage, and virtual private networks (VPNs).
Multi-factor authentication
Regardless of how arts organizations are storing their information, multi-factor authentication (MFA) is a way to increase security for employees accessing the organization’s network. Many people have experienced some use of MFA—one example is when you log into an account with a username and password and you are automatically sent a confirmation via text or email. The three nonprofit arts IT professionals I talked to all said they use MFA for some aspect of their network, including Microsoft email and cloud storage and a mobile device manager (which will be discussed later). When choosing solutions for your organization, consider if they offer MFA for enhanced security and see if MFA is an option on your organization’s current platforms. Microsoft 365, for example, allows you to set up multi-factor authentication.
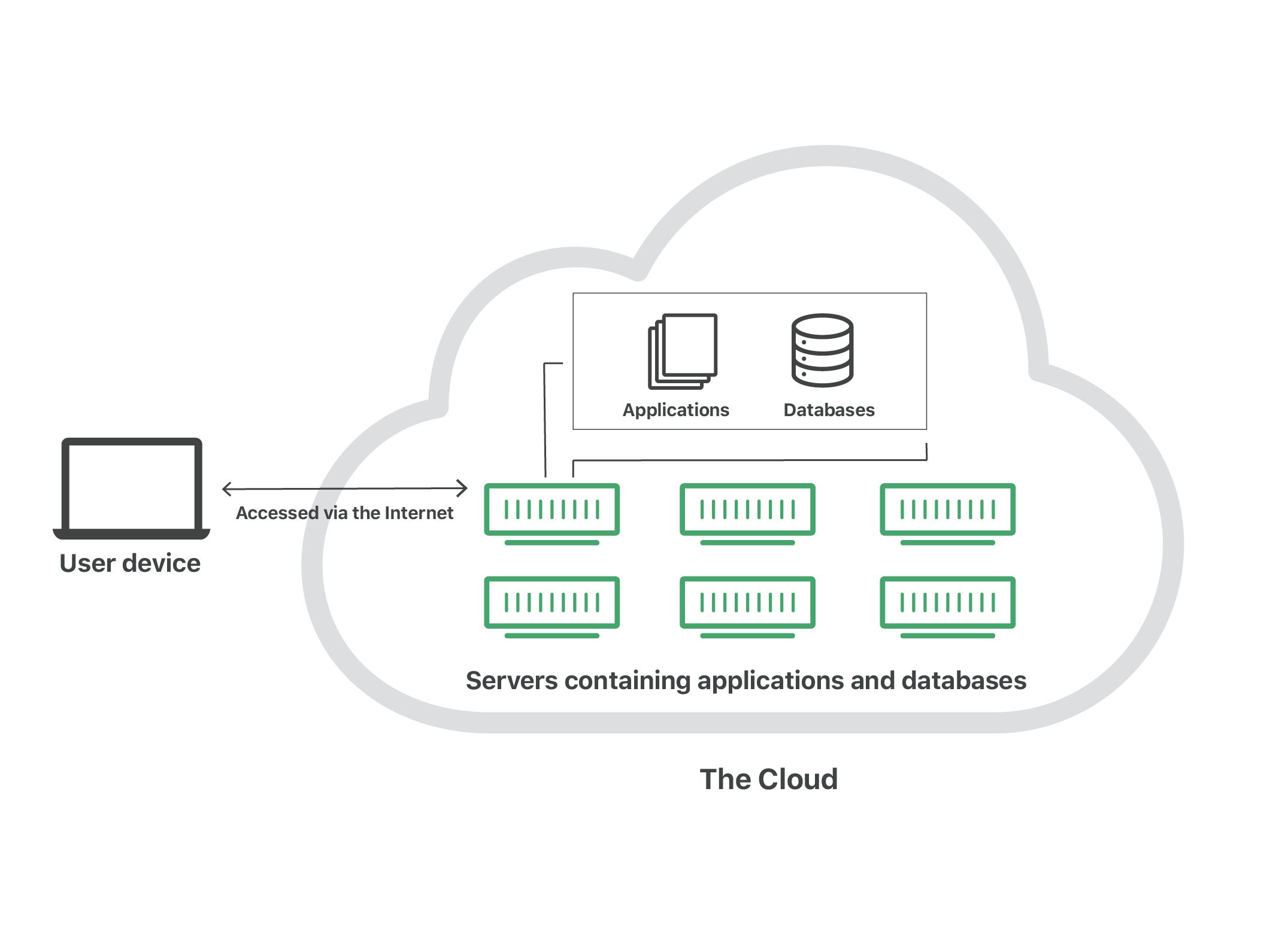
Cloud storage
Cloud storage is a long-term solution for arts nonprofits that would allow employees to securely access files anywhere and everywhere. It eliminates the need to manage storage hardware and worry about how people would access the information on it when out of the office. Cloud storage has many benefits for nonprofits, including that it makes data more secure since it is “built to meet the requirements of the most security-sensitive organizations.” An organization can set up different login credentials with unique access to different levels of data. Additionally, since the physical container is eliminated, it prevents the possibility of information going missing or being destroyed by any natural disaster.
Figure 2: Diagram of the cloud. Source: Cloudflare.
As indicated by Blackbaud’s recent breach, affecting several arts organizations, it is important to make sure that a cloud storage provider has protocols for the case of a security breach when choosing this storage alternative. Blackbaud, a cloud software company, was hit with a ransomware attack in May 2020 through which hackers were able to steal private information from 200 institutions’ donor lists. Although Blackbaud paid the undisclosed ransom amount in Bitcoin to ensure that the data was destroyed and not distributed, the company merely took the hackers at their word that the stolen data was destroyed. According to Artnet, cybersecurity professional Tyler Cohen Wood “advises that museums employing third-party providers familiarize themselves with the company’s procedures for handling ransomware attacks and to have secure data backups, even if that means paying extra.” TechSoup has a handy comparison chart of features offered by various cloud storage providers, including each one’s cybersecurity measures.
Virtual private network
A VPN allows employees to bypass geographic restrictions to gain access to a network and also encrypts all of the device’s internet traffic, keeping activity private no matter where someone is. This is a very secure solution for remote work since some outside risks, such as what Wi-Fi network one is using, are eliminated since encryption protects users’ online activities.
Using a VPN requires vigilance around who accesses it and on what devices since it provides access to internal organizational networks and many have limits on the number of devices that can access them. One museum system with 500 remote employees doesn’t allow VPN access through devices outside of the organization. Another organization with 85 staff working from home only allows a limited number of employees to access the VPN, and gaining access requires submitting a request through a supervisor and being educated about how to use a VPN.
Two of the organizations I talked to that use a VPN set it up from the same company as their firewalls for simplicity. TechSoup also provides some additional VPN options and considerations here.
Figure 3: Illustration of how a VPN works. Source: TechSoup.
3. Implementing policies and procedures for using personal devices
The most secure solution for employees using personal devices for remote work is to avoid their use as much as possible. According to Sean Mooney with Cybereason, “personal devices often lack the strong antivirus software, customized firewalls, and automatic online backup tools built in to business networks.” Additionally, because many people often take their devices with them wherever they go, they are vulnerable to being misplaced or picked up by someone else.
In a best-case scenario, all nonprofit arts organizations would have the capacity to provide employees with computers for working from home. With limited resources, however, this is not always the case. One museum I talked to was able to repurpose laptops from classrooms for employees’ use. If eliminating the use of personal devices is not possible, though, some ways to mitigate the risks involved are bring-your-own device (BYOD) policies and mobile device management software.
Bring-your-own device policy
When establishing how employees can use personal devices for remote work, it is important for organizations to create a bring-your-own device (BYOD) policy. Many organizations have this in non-pandemic times. One interviewee who works in IT for an orchestra pointed out that he always considers musicians as remote employees since they do not have office space, but still access organizational information from their personal devices. The organization uses a BYOD policy to ensure that musicians use their devices securely.
BYOD policies should include what employees can use their personal devices for and the security measures that should be used on those devices. Dan Lautman with Delcor identifies four levels of BYOD security for associations and nonprofits, ranging from requiring a four-digit passcode on the device to not allowing any personal devices and using mobile device management software (addressed in the next section). The updated Nonprofit Technology Policy Workbook also contains a section about creating a BYOD policy.
Mobile device management
Mobile device management (MDM) “[provides] a single platform where all mobile devices in use can be monitored and managed” and contains user authorization features. MDM software can be used by organizations allowing employees to use personal devices and for those that have issued organization devices. One MDM software solution that came up in my interviews was Microsoft Intune, which is convenient for those who already use Microsoft products at their organization. Like other MDM software, with Intune, you can control how your organization’s devices are used, including preventing emails from being sent to people outside the organization. Intune allows settings to be configured differently for personal devices versus the organization’s devices since employees wouldn’t want to give up complete control of their smart phone, for example.
4. Training employees on Best Practices
An important component of all of these cybersecurity solutions and risks is human action: people in the organization need to be on board with acting safely. Each of the people that I interviewed had employee education and training in place to some capacity. This can include test phishing emails and general PSAs.
When sending out test phishing emails, organizations would want to know the results of the test and know what steps they need to take to make employees more aware of cybersecurity risks. Software exists to help organizations send automated tests. Many of these tools also take recipients directly to a training module when they click and provide a diagnostic report to managers. One tool that came up when talking to IT professionals in the arts nonprofits sector was KnowBe4. It has paid security training products and services and also some free tools, including a free phishing security test that would allow managers to get a baseline idea of where their organization stands.
According to one interviewee, they implemented training “because people need to know what to look for.” This is especially true in the context of the pandemic. Compared to pre-coronavirus numbers, cyberattacks have increased by 400%. Phishing attacks, specifically, prey on people’s fears and uncertainties, and with new buzzwords in our lexicon like “quarantine,” “contact tracing,” etc., people can be easily drawn to click, which is why training people on what exactly to look for is important. With these new threats in mind, some organizations I talked to have increased their training and phishing tests to at least quarterly.
Conclusion
While addressing cybersecurity can seem like it includes an overwhelming number of things to consider, the main objective is to allow employees to safely work to accomplish the organization’s mission. Those working to boost cybersecurity in arts nonprofits should work to understand what employees are trying to achieve and be a good partner while educating coworkers about why cybersecurity is important and how different solutions can help.
This is not an exhaustive list of what would lead an organization to having strong cybersecurity in normal operations, but provides a starting place for remote work. Which solutions work best for an organization varies by size and budget, but all organizations could gain from increasing their long-term investment in digital security.
Resources
American Alliance of Museums. “Safety First: How museums can embrace cyber-security opportunities and risks with open arms.” May 1, 2018. https://www.aam-us.org/2018/05/01/safety-first-how-museums-can-embrace-cyber-security-opportunities-and-risks-with-open-arms/.
Beyond Security. “How to Manage Your Employees’ Devices When Remote Work Has Become the Norm.” March 2020, https://blog.beyondsecurity.com/how-to-manage-your-employees-devices-when-remote-work-has-become-the-new-norm/.
Cuseum. “3 Reasons Why Museums and Nonprofits Should Be Thinking About Cybersecurity.” October 21, 2019. https://cuseum.com/blog/2019/10/21/3-reasons-why-museums-and-nonprofits-should-be-thinking-about-cybersecurity.
Eshleman, Matt. “Nonprofit Cybersecurity: A Guide for 2020.” Community IT Innovators. https://communityit.com/nonprofit-cybersecurity/.
Gluck, Jamin. “How Can Cloud Storage Benefit My Nonprofit?” Tech Soup, July 11, 2018. https://blog.techsoup.org/posts/how-can-cloud-storage-benefit-my-nonprofit-techsoup.
Hulshof-Schmidt, Robert. State of Nonprofit Cybersecurity. NTEN, November 2018. https://www.nten.org/wp-content/uploads/2018/11/Cybersecurityreport2018NTEN.pdf.
Lautman, Dan. “BYOD Security Options for Associations & Nonprofits.” Delcor, January 5, 2018. https://www.delcor.com/resources/blog/byod-security-options-for-associations-nonprofits.
Microsoft. “Microsoft Intune is an MDM and MAM provider for your devices.” Documentation, June 23, 2020. https://docs.microsoft.com/en-us/mem/intune/fundamentals/what-is-intune.
Miller, Maggie. “Lawmakers introduce legislation to boost cybersecurity of local governments, small businesses.” The Hill, September 25, 2020. https://thehill.com/policy/cybersecurity/518267-lawmakers-introduce-legislation-to-boost-cybersecurity-of-local.
MonsterCloud. “Top Cybersecurity Experts Report: 4,000 Cyber Attacks a Day Since COVID-19 Pandemic.” PR Newswire, August 11, 2020. https://www.prnewswire.com/news-releases/top-cyber-security-experts-report-4-000-cyber-attacks-a-day-since-covid-19-pandemic-301110157.html.
Mooney, Sean. “Cyber Security Tips for Allowing Employees to Work From Home.” Cybereason, August 20, 2020. https://www.cybereason.com/blog/cyber-security-tips-for-allowing-employees-to-work-from-home.
National Conference of State Legislatures. “Security Breach Notification Laws.” Research. June 17, 2020. https://www.ncsl.org/research/telecommunications-and-information-technology/security-breach-notification-laws.aspx.
Nield, David and Brian Turner. “Best MDM solutions in 2020: Mobile Device Management for BYOD policies.” Tech Radar Pro, November 26, 2020. https://www.techradar.com/best/best-mdm-solutions.
Porup, J.M. “12 cheap or free cybersecurity training resources.” CSO, April 28, 2020. https://www.csoonline.com/article/3340819/7-cheap-or-free-cybersecurity-training-resources.html.
Pryor, Wendy. “Staying Safe: Cybersecurity in Modern Museums.” MW17: Museums and the Web 2017. https://mw17.mwconf.org/paper/staying-safe-cybersecurity-in-modern-museums-internal-external-and-hidden-threats-with-a-focus-on-cryptography-to-maintain-data-security/.
Symanovich, Steve. “What is a VPN?” Norton, “Privacy,” October 27, 2020. https://us.norton.com/internetsecurity-privacy-what-is-a-vpn.html.
Tech Impact. “Nonprofit Technology Policy Workbook.” August 2020. https://f.hubspotusercontent20.net/hubfs/575821/TECH%20IMPACT%20IDEALWARE%20NP%20POLICY%20WORKBOOK%20081920.pdf.