Infographic of top cloud concerns, per a 2012 CloudPassage survey.
Last April, Google leapt into the personal cloud storage market with Google Drive, its answer to popular services like Dropbox and Microsoft’s SkyDrive. However, soon after this much anticipated launch came a wave of outrage. Users picking through the terms of service had discovered a troubling paragraph:
“When you upload or otherwise submit content to our Services, you give Google (and those we work with) a worldwide license to use, host, store, reproduce, modify, create derivative works (such as those resulting from translations, adaptations or other changes we make so that your content works better with our Services), communicate, publish, publicly perform, publicly display and distribute such content. The rights you grant in this license are for the limited purpose of operating, promoting, and improving our Services, and to develop new ones.”
Accusations swirled that Google intended to steal user’s data and use it for their own nefarious purposes. But these digital sleuths had skipped over an important clue, the prior paragraph which reads, “Some of our Services allow you to submit content. You retain ownership of any intellectual property rights that you hold in that content. In short, what belongs to you stays yours.”
Writers such as The Verge’s Nilay Patel went on to show that other cloud storage providers defined functionally identical permissions as conditions of using their services. But although this particular situation turned out in some respects to be much ado about nothing, it is exactly the sort of cloud issue arts organizations must pay attention to since they will, by the nature of their work, handle a wide variety of creative intellectual property that should be carefully protected from unauthorized access or distribution.
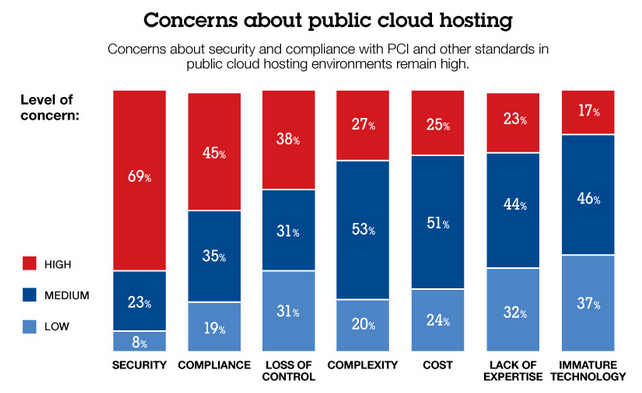
When it comes to the cloud, security is a widespread concern across sectors. According to a recent survey, conducted by Lockheed Martin and the Cyber Security Alliance, security was listed as the top concern by Government IT decision makers, despite overall increasing adoption of cloud technology. Security is a multifaceted issue, ranging from the above example concerning what rights are retained when information is uploaded to the cloud, to more classical issues involving data theft. The basic fact is that when organizations take their data into the cloud they are ceding day-to-day control of that data. Though they can access it and share it at will, they typically will have no idea in which physical datacenter, or even in which country, their files are currently stored. Users must rely on the provider to not just manage their data responsibly, and to prevent loss of their data through hardware failure, but to keep their data encrypted and inaccessible to unauthorized users.
Regardless of this expectation, breaches can and do occur. Over just the past two years Dropbox has suffered two separate major security failures. On June 19, 2011 any account could be accessed with any password for nearly four hours. Dropbox worked hard to contact potentially affected users and alert them of the breach, but it was a major issue caused by a seemingly minor code update. On July 16, 2012 users began complaining about a bombardment of spam, later traced to a stolen customer email list acquired from a compromised Dropbox employee’s account. Sony was the victim of a massive attack in 2011 which led to the theft of millions of usernames, passwords, and even credit card information.
My intention in highlighting these breaches isn’t to pick on Dropbox or Sony. Rather it’s to make the point that, despite advantages in redundancy and accessibility, any use of cloud services moves data out of users’ direct control and increases the potential for exposure to these kind of large scale events. Compared to thefts of actual computer hardware, major data heists are comparatively rare, but minimizing overall risk exposure should be the goal of an organization’s security policy.
While it is certainly in the interest of cloud providers to make security improvements on the backend in order to minimize incidents of theft, as such events are potentially catastrophic to their brand identity and consumer trust, cloud users can also take responsibility for safeguarding their data. Here are a few steps simple steps:
· “Two-step authentication,” as profiled here by Mashable’s Christina Warren, gives an extra layer of protection, especially when your accounts are accessed by unrecognized by devices. Rather than simply logging in with your username and password, two-step verification either emails or texts an additional verification code before allowing login. Typically the second step is only required once a month per device, allowing a window of time where a device is “trusted”.
· Strong and unique passwords. Services like LastPass, 1Password, and Dashlane offer a means of generating and managing unique passwords for all of your online accounts. Avoiding password duplication eliminates the risk of one stolen password causing a cascade of thefts, as data thieves often attempt to use stolen credentials on other services in hopes of discovering banking or other sensitive information. Additionally, these services all ensure that password decryption is handled locally, so it’s not simply a matter of replacing one cloud risk with another.
· Above all, carefully consider if your data needs to be stored online. While you need not issue a blanket prohibition on uploading sensitive intellectual property or customer information, it’s well worth understanding the possible consequences of data theft before doing so. If privacy is particularly important and you are looking to just store files, one solution is to encrypt the archived files before uploading them.
Security is always an important issue when it comes to digital data, but the takeaway from this article isn’t to avoid the cloud. Rather, use it wisely. Cloud service providers typically have teams dedicated to security and data monitoring, and technological resources far exceeding those of nonprofit arts organizations. After all, the entire business model of the cloud hinges on secure service delivery. By carefully considering which data are stored in the cloud and who has regular access to that data, overall risk can be minimized.